Deep Dive Into SectopRat


Hello World, Today Will Gonna Explain a lovely topic for me which is assembly and specifically dos assembly. So lets go without further delays.
What’s Assembly:
So Assembly is just a programming language but its a very very low level one. why its low level well because u mostly dealing with registers, interrupts u are actually dealing with the CPU u are talking to it directly actually there another more low level layer which microcode which is basically a interface between your assembly language / instructions and the hardware.
How Assembly Assembles to Machine Code:
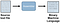
Well so as we said assembly is just a programming language and programming languages in general are tools to talk to a computer without needing to write machine code , but the computer only understands machine code so we need a way to assemble our assembly code into machine code, that’s what an Assembler its main job in life is take your assembly code convert it to machine code that’s it. But there is actually another step needed in order to run your executable why didn’t we assembled the code and everything is fine yes it is but that returns to what actually the assembler produces the assembler don’t produce the final executable it produces a specific type of files called Object Files with extension “.obj” on windows on Linux its .o I think. so we need another program in order to generate our final executable which is the linker’s job this image actually explains this concept very well.

Registers:
So registers are just small but fast memory spaces inside the CPU , while understanding assembly language for reverse engineering & low level understanding of stuffs . Registers are fastest memory spaces in the computer its quite easily accessible and they are even faster than RAM, one can imagine it like a CPU tool chain at the end of the day we will just store and manipulate data in them I will explain the types of them while writing our first Hello World Program :).
Prerequisites:
MASM (Microsoft Assembler)
DosBox (MS-DOS Emulator we will use it alot another option is using emu8086)
Make sure to install both in the C Drive. Now open DosBox and follow with me First mount to C:\8086 folder with this command
mount c C:\8086 (u must make sure the folder is in the C Drive and its named 8086)
No Just type c: and then edit helloworld.asm
and we are ready to go and write our program. I will write the code and then explain it line by line. here u go
- .model small
- .stack 100h
- .data
- hello db 10,13,”Hello World$”
- .code
- main proc
- lea dx, hello
- mov ah, 9h
- int 21h
- main endp
- end main
So now save the code and now you must first assemble it then link it , which makes it an executable which u can run
To Compiler: masm <name_of_source>;
To Link: link <name_of_source>; ( don’t put .asm at the end)
So Let's Go Step by Step.
.model small = this describes the memory model or how the ram is organized so basically there is two types of pointers far pointer and near pointer the near pointer points to data in the current segment its relative to the data segment registers they have size of 16 bits, on the other hand far pointer typically pi= points to another segment read this for more info.
.stack = is the specifying the stack here we are allocating 100 bytes. main proc is our main procedure like main function in C.
.data = so here we put constant, global variables etc…
.code = tell the assembler its the beginning of our code
. lea dx, hello = lea will load the address of our hello world message into a special register dx and this register is used as a pointer to the data section
. mov ah, 9h = let’s first discuss the ax register its a 16 bit register 8 bit high and 8bit low ah is the high 8 bits whenever u want to do some function u will move a specific constant into this register so here 9h is for printing data, al is the lower 8 bit and its used for others stuff like arithmetic. u can see a list of dos interrupts here DOS Interrupts
. int 21h = is causing and interrupt and returning to dos an interrupt is for telling interrupts the cpu or it tells it stop whatever u are doing and do what I asked for for our case its printing to screen.
The rest of the code is self explanatory & easy to understand :). I suggest you to go through this articles by @daax_rynd Applied Reverse Engineering Series and for more dos assembly u can read Giant Book of Computer Viruses and watch this series . This blog was just a small glimpse of assembly language . My upcoming posts will be based on reverse engineering & malware analysis ! Till then happy debugging !